- Headteacher / Senior Leaders
- School Development Leaders
- Staff – including teachers, support staff, technical staff
- Parents/Carers
Schedule for Development / Monitoring / Review
| This Online Safety policy was issued in: | December 2017 |
| The implementation of this Online Safety policy
will be monitored by: |
Mr Gulam Hussain (Head Teacher)
Mr Sameer Abbas (Chair) |
| The Online Safety Policy will be reviewed every two years, or more regularly in the light of any significant new developments in the use of the technologies, new threats to online safety or incidents that have taken place. The next
anticipated review date will be: |
September 2023 or sooner if necessary |
| Should serious online safety incidents take place, the following external persons / agencies should be informed: | Gulam Abbas Hussain Hanila Syed
Farhana Begum Maria Kashif |
The school will monitor the impact of the policy using:
- Logs of reported incidents
- Monitoring logs of internet activity (including sites visited) / filtering
- Internal monitoring data for network activity
This policy applies to all members of the school’s community (including staff, students / pupils, volunteers, parents / carers) who have access to and are users of school ICT systems, both in and out of the school.
The Education and Inspections Act 2006 empowers Headteacher to such extent as is reasonable, to regulate the behaviour of pupils when they are off the school site and empowers members of staff to impose disciplinary penalties for inappropriate behaviour. This is pertinent to incidents of cyber- bullying or other Online Safety incidents covered by this policy, which may take place outside of the
school, but is linked to membership of the school. The 2011 Education Act increased these powers with regard to the searching for and of electronic devices and the deletion of data (see appendix for template policy). In the case of both acts, action can only be taken over issues covered by the school’s Behaviour Policy.
Read Academy will deal with such incidents within this policy and associated behaviour and anti- bullying policies and will, where known, inform parents / carers of incidents of inappropriate online safety behaviour that take place out of school.
The following section outlines the online safety roles and responsibilities of individuals and groups within the school.
3.1. School Development Leaders (SDL’s):
The SDL’s are responsible for the approval of the Online Safety Policy and for reviewing the effectiveness of the policy. This will be carried out by them receiving regular information about online safety incidents and monitoring reports. The Chair has taken on the role of Online Safety officer. The role of the Online Safety officer will include:
- regular monitoring of online safety incident logs
- regular monitoring of filtering / change control logs
- reporting to relevant meeting
- keeping up to date with legislations relating to safeguarding and e-safety.
3.2. Headteacher and Senior Leaders:
- The Headteacher has a duty of care for ensuring the safety (including online safety) of members of the school community, though the day-to-day responsibility for online safety will be delegated to the senior leadership team and safeguarding
- The Headteacher and (at least) another member of the senior leadership team should be aware of the procedures to be followed in the event of a serious online safety allegation being made against a member of
- The Headteacher and Senior Leaders are responsible for ensuring that the Online Safety Coordinator / Officer and other relevant staff receive suitable training to enable them to carry out their online safety roles and to train other colleagues, as
- The Headteacher / Senior Leaders will ensure that there is a system in place to allow for monitoring and support of those in school who carry out the internal online safety monitoring role. This is to provide a safety net and also support to those colleagues who take on important monitoring
- The senior leadership team will receive regular monitoring reports from the Online Safety Co-ordinator /
3.3. Network Manager
The Network Manager is responsible for ensuring:
- that the school’s technical infrastructure is secure and is not open to misuse or malicious attack
- that the school meets required online safety technical requirements and any Local Authority Online Safety Policy / Guidance that may
- that users may only access the networks and devices through a properly enforced password protection in which passwords are regularly
- that they keep up to date with online safety technical information in order to effectively carry out their online safety role and to inform and update others as
- that the use of the network / internet / Learning Platform / remote access / email is regularly monitored in order that any misuse / attempted misuse can be reported to the Headteacher for investigation / action /
3.4. Teaching and Support Staff
Are responsible for ensuring that:
- they have an up-to-date awareness of online safety matters and of the current school Online Safety Policy and
- they have read and understood the Staff Acceptable Use Policy / Agreement (AUP)
- they report any suspected misuse or problem to the Headteacher for investigation / action / sanction
- all digital communications with pupils / parents / carers should be on a professional level and only carried out using official school
- online safety issues are embedded in all aspects of the curriculum and other activities
- pupils understand and follow the Online Safety Policy and acceptable use policies
- pupils have a good understanding of research skills and the need to avoid plagiarism and uphold copyright
- they monitor the use of digital technologies, mobile devices, cameras etc in lessons and other school activities (where allowed) and implement current policies with regard to these devices
- in lessons where internet use is pre-planned, pupils should be guided to sites checked as suitable for their use and that processes are in place for dealing with any unsuitable material that is found in internet
3.5. Designated Safeguarding Lead
Should be trained in Online Safety issues and be aware of the potential for serious child protection / safeguarding issues to arise from:
- sharing of personal data
- access to illegal / inappropriate materials
- inappropriate on-line contact with adults / strangers
- risk of radicalisation (refer to prevent risk assessment)
- potential or actual incidents of grooming
- cyber-bullying
3.6. Pupils:
- are responsible for using the school digital technology systems in accordance with the Pupil Acceptable Use Agreement
- have a good understanding of research skills and the need to avoid plagiarism and uphold copyright regulations
- need to understand the importance of reporting abuse, misuse or access to inappropriate materials and know how to do so
- will be expected to know and understand policies on the use of mobile devices and digital cameras. They should also know and understand policies on the taking / use of images and on cyber-bullying.
- should understand the importance of adopting good online safety practice when using digital technologies out of school and realise that the school’s Online Safety Policy covers their actions out of school, if related to their membership of the
3.7. Parents / Carers
Parents / Carers play a crucial role in ensuring that their children understand the need to use the internet / mobile devices in an appropriate way. The school will take every opportunity to help parents understand these issues through parents’ evenings, newsletters, letters, website / Learning Platform and information about national / local online safety campaigns / literature. Parents and carers will be encouraged to support the school in promoting good online safety practice and to follow guidelines on the appropriate use of:
- digital and video images taken at school events
- access to parents’ sections of the website / Learning Platform and on-line student / pupil records
- their children’s personal devices in the school (where this is allowed)
4.1. Education – Pupils
Whilst regulation and technical solutions are very important, their use must be balanced by educating pupils to take a responsible approach. The education of pupils in online safety is therefore an essential part of Read Academy’s online safety provision. Children need the help and support of the school to recognise and avoid online safety risks and build their resilience.
Online safety should be a focus in all areas of the curriculum and staff should reinforce online safety messages across the curriculum. The online safety curriculum should be broad, relevant and provide progression, with opportunities for creative activities and will be provided in the following ways:
- A planned online safety curriculum should be provided as part of Computing / PHSE / other lessons and should be regularly revisited this is done during the first week or during ‘SAFETY WEEK’
- Key online safety messages should be reinforced as part of a planned programme of assemblies and tutorial / pastoral activities
- Pupils should be taught in all lessons to be critically aware of the materials / content they access on-line and be guided to validate the accuracy of
- Pupils should be taught to acknowledge the source of information used and to respect copyright when using material accessed on the internet
- Pupils should be supported in building resilience to radicalisation by providing a safe environment for debating controversial issues and helping them to understand how they can influence and participate in decision-making.
- Pupils should understand the risk of radicalisation and the prevent lead is to ensure a lesson per year group is delivered from a prevent trained officer, a workshop for parents is also to be
- Pupils should be helped to understand the need for the pupil Acceptable Use Agreement and encouraged to adopt safe and responsible use both within and outside
- Staff should act as good role models in their use of digital technologies the internet and mobile devices
- In lessons where internet use is pre-planned, pupils are always guided to sites checked as suitable for their use and that processes are in place for dealing with any unsuitable material that is found in internet
- Where pupils are allowed to freely search the internet, staff remain vigilant in monitoring the content of the websites where they
- It is accepted that from time to time, for good educational reasons, pupils may need to research topics (e.g. racism, drugs, discrimination) that would normally result in internet searches being blocked. In such a situation, staff can request that the Technical Staff (or other relevant designated person) can temporarily remove those sites from the filtered list for the period of study. Any request to do so, should be auditable, with clear reasons for the need to the head teacher.
4.2. Education – Parents / Carers
Many parents/carers have only a limited understanding of online safety risks and issues, yet they play an essential role in the education of their children and in the monitoring / regulation of the children’s on-line behaviours. Parents/carers may underestimate how often children and young people come across potentially harmful and inappropriate material on the internet and may be unsure about how to respond.
At Read Academy we will seek to provide information and awareness to parents and carers through:
- Letters, newsletters, web site
- Parents / Carers evenings / sessions
- High profile events / campaigns e.g. Safety week
4.3. Education & Training – Staff / Volunteers
It is essential that all staff receive online safety training and understand their responsibilities, as outlined in this policy. Training will be offered as follows:
- A planned programme of formal online safety training will be made available to staff. This will be regularly updated and reinforced during INSETS and
- All new staff should receive online safety training as part of their induction programme, ensuring that they fully understand the school internet Safety Policy and Acceptable Use Agreements.
- It is expected that some staff will identify online safety as a training need within the performance management
- The Online Safety Coordinator / Officer (safeguarding officer) or other nominated person) will receive regular updates through attendance at training events and from other relevant organisations) and by reviewing guidance documents released by relevant
- This Online Safety Policy and its updates will be presented to and discussed by staff in staff / team meetings / INSET
- The Online Safety Coordinator / Officer will provide advice / guidance / training to individuals as required.
The school will be responsible for ensuring that the school network is as safe and secure as is reasonably possible and that policies and procedures approved within this policy are implemented. It will also need to ensure that the relevant people named in the above sections will be effective in carrying out their online safety responsibilities:
- School technical systems will be managed in ways that ensure that it meets recommended technical requirements
- Servers, wireless systems and cabling must be securely located and physical access restricted
- All users will have clearly defined access rights to school technical systems and devices
- The “master / administrator” passwords for the school ICT system, used by the Network Manager (or another person) must also be available to the Headteacher and/or other nominated senior leader and kept in a secure place
- The Headteacher is responsible for ensuring that software licence logs are accurate and up to date and that regular checks are made to reconcile the number of licences purchased against the number of software installations
- Internet access is filtered for all users. Illegal content (child sexual abuse images) is filtered by the broadband and firewall
- Internet filtering should ensure that children are safe from terrorist and extremist material when accessing the internet
- Pupils have no access to computers or laptops without the supervision of an adult staff present. All laptops are kept locked when not in use. Pupils are never left unattended when access to computer is given in class, scheduled times are allocated on the weekly class timetable for the computing lessons and cross curricular subjects. All staff are reminded regularly of the dangers present if pupils are left unattended with access to internet. Pupils will be regularly reminded of the dangers and safe use of ICT; E safety will be regularly mentioned to pupils throughout the academic
- Appropriate security measures are in to protect the servers, firewalls, routers, wireless systems, work stations, mobile devices etc from accidental or malicious attempts which might threaten the security of the school systems and data. These are tested regularly. The school infrastructure and individual workstations are protected by up to date virus
- All temporary staff will need to read school internet and safeguarding policy for the provision of temporary access of “guests” (e.g. trainee teachers, supply teachers, visitors) onto the school systems.
- An agreed policy is in place regarding the extent of personal use that users (staff / students / pupils / and their family members are allowed on school devices that may be used out of school.
An agreed policy is in place that allows staff to / forbids staff from downloading executable files and installing programmes on school devices.
Mobile technology devices may be school owned/provided or personally owned and might include: smartphone, tablet, notebook / laptop or other technology that usually has the capability of utilising the school’s wireless network. The device then has access to the wider internet which may include the school’s learning platform and other cloud-based services such as email and data storage.
All users should understand that the primary purpose of the use mobile / personal devices in a school context is educational. The mobile technologies policy should be consistent with and inter- related to other relevant school polices including but not limited to the Safeguarding Policy, Behaviour Policy, Bullying Policy, Acceptable Use Policy, and policies around theft or malicious damage. Teaching about the safe and appropriate use of mobile technologies should be an integral part of the school’s online safety education programme.
The school Acceptable Use Agreements for staff, pupils/students and parents/carers will give consideration to the use of mobile technologies. The school allows:
| School Devices | Personal Devices | |||
| School owned for single user | School owned for multiple users | Staff owned | Visitor owned | |
| Allowed in school | Yes | Yes | If Approved | If Approved |
| Full network access | Yes | Yes | No | No |
| Internet only | Yes | Yes | Yes | No |
Aspects that the school may wish to consider are included in the Online Safety Policy and Acceptable Use Agreements:
School owned / provided devices:
- Who they will be allocated to
- Where, when and how their use is allowed – times / places / in school / out of school
- If personal use is allowed
- Levels of access to networks / internet (as above)
- Management of devices / installation of apps / changing of settings / monitoring
- Network / broadband capacity
- Technical support
- Filtering of devices
- Access to cloud services
- Data Protection
- Taking / storage / use of images
- Exit processes – what happens to devices / software / apps / stored data if user leaves the school
- Liability for damage
- Staff training
Personal devices:
- Which users are allowed to use personal mobile devices in school (staff / pupils / visitors)
- Restrictions on where, when and how they may be used in school
- Storage
- Whether staff will be allowed to use personal devices for school business
- Levels of access to networks / internet (as above)
- Network / broadband capacity
- Technical support (this may be a clear statement that no technical support is available)
- Filtering of the internet connection to these devices
- Data Protection
- The right to take examine and search user’s devices in the case of misuse (England only)
- Taking / storage / use of images
- Liability for loss/damage or malfunction following access to the network (likely to be a disclaimer about school responsibility).
- Identification / labelling of personal devices
- How visitors will be informed about school requirements
- How education about the safe and responsible use of mobile devices is included in the school online safety education
The development of digital imaging technologies has created significant benefits to learning, allowing staff and pupil’s instant use of images that they have recorded themselves or downloaded from the internet. However, staff, parents / carers and pupils need to be aware of the risks associated with publishing digital images on the internet. Such images may provide avenues for cyberbullying to take place. Digital images may remain available on the internet forever and may cause harm or embarrassment to individuals in the short or longer term. It is common for employers to carry out internet searches for information about potential and existing employees. The school will inform and educate users about these risks and will implement policies to reduce the likelihood of the potential for harm:
• When using digital images, staff should inform and educate pupils about the risks associated with the taking, use, sharing, publication and distribution of images. In particular they should recognise the risks attached to publishing their own images on the internet e.g. on social networking sites.
• Written permission from parents or carers will be obtained before photographs of pupils are published on the school website / social media / local press (see Parents / Carers Acceptable Use Agreement
• In accordance with guidance from the Information Commissioner’s Office, parents / carers are welcome to take videos and digital images of their children at school events for their own personal use (as such use in not covered by the Data Protection Act). To respect
everyone’s privacy and in some cases protection, these images should not be published / made publicly available on social networking sites, nor should parents / carers comment on any activities involving other pupils in the digital / video images.
• Staff and volunteers are allowed to take digital / video images to support educational aims, but must follow school policies concerning the sharing, distribution and publication of those images. Those images should only be taken on school / academy equipment, the personal equipment of staff should not be used for such purposes.
• Care should be taken when taking digital / video images that pupils are appropriately dressed and are not participating in activities that might bring the individuals or the school into disrepute.
• pupils must not take, use, share, publish or distribute images of others without their permission
• Photographs published on the website, or elsewhere that include students / pupils will be selected carefully and will comply with good practice guidance on the use of such images.
• Pupil’s full names will not be used anywhere on a website or blog, particularly in association with photographs.
• Pupil’s work can only be published with the permission of the pupil and parents/carers.
Personal data will be recorded, processed, transferred and made available according to the Data Protection Act 1998 which states that personal data must be:
- Fairly and lawfully processed
- Processed for limited purposes
- Adequate, relevant and not excessive
- Accurate
- Kept no longer than is necessary
- Processed in accordance with the data subject’s rights
- Secure
- Only transferred to others with adequate
At Read Academy we ensure that:
- It will hold the minimum personal data necessary to enable it to perform its function and it will not hold it for longer than necessary for the purposes it was collected
- Every effort will be made to ensure that data held is accurate, up to date and that inaccuracies are corrected without unnecessary
- All personal data will be fairly
Staff must ensure that they:
- At all times take care to ensure the safe keeping of personal data, minimising the risk of its loss or
- Use personal data only on secure password protected computers and other devices, ensuring that they are properly “logged-off” at the end of any session in which they are using personal data.
- Transfer data using encryption and secure password protected
When personal data is stored on any portable computer system, memory stick or any other removable media:
- the data must be encrypted and password protected
- the device must be password protected
- the device must offer approved virus and malware checking software
- the data must be securely deleted from the device, in line with school policy (below) once it has been transferred or its use is complete
Communications:
A wide range of rapidly developing communications technologies has the potential to enhance learning. When using communication technologies, the school considers the following as good practice:
- The official school email service may be regarded as safe and secure and is monitored. Users should be aware that email communications are monitored. Staff and pupils should therefore use only the school email service to communicate with others when in school, or on school systems (e.g. by remote access).
-
- Users must immediately report, to the nominated person –the receipt of any communication that makes them feel uncomfortable, is offensive, discriminatory, threatening or bullying in nature and must not respond to any such
- Any digital communication between staff, pupils or parents / carers (email, social media, chat, blogs, VLE etc.) must be professional in tone and content. These communications may only take place on official (monitored) school systems. Personal email addresses, text messaging or social media must not be used for these
- Whole class / group email addresses may be used at KS1, while pupils at KS2 onwards will be provided with individual school email addresses for educational
- Pupils should be taught about online safety issues, such as the risks attached to the sharing of personal details. They should also be taught strategies to deal with inappropriate communications and be reminded of the need to communicate appropriately when using digital technologies.
- Personal information should not be posted on the school website and only official email addresses should be used to identify members of
Read Academy provides the following measures to ensure reasonable steps are in place to minimise risk of harm to pupils, staff and the school through:
- Ensuring that personal information is not published
- Training is provided including: acceptable use; social media risks; checking of settings; data protection; reporting issues
- Clear reporting guidance, including responsibilities, procedures and sanctions
- Risk assessment, including legal risk
School staff should ensure that:
- No reference should be made in social media to pupils, parents / carers or school staff
- They do not engage in online discussion on personal matters relating to members of the school community
- Personal opinions should not be attributed to the school
- Security settings on personal social media profiles are regularly checked to minimise risk of loss of personal information
When official school social media accounts are established, there should be:
- A process for approval by senior leaders
- Clear processes for the administration and monitoring of these accounts – involving at least two members of staff
- A code of behaviour for users of the accounts, including systems for reporting and dealing with abuse and misuse
- Understanding of how incidents may be dealt with under school disciplinary procedures
Personal Use:
- Personal communications are those made via a personal social media account. In all cases, where a personal account is used which associates itself with the school or impacts on the school, it must be made clear that the member of staff is not communicating on behalf of the school with an appropriate disclaimer. Such personal communications are within the scope of this policy
- Personal communications which do not refer to or impact upon the school are outside the scope of this policy
- Where excessive personal use of social media in school is suspected, and considered to be interfering with relevant duties, disciplinary action may be taken
- The school permits reasonable and appropriate access to private social media sites
Monitoring of Public Social Media:
- As part of active social media engagement, it is considered good practice to pro-actively monitor the Internet for public postings about the school
- The school should effectively respond to social media comments made by others according to a defined policy or process
The school’s use of social media for professional purposes will be checked regularly by the senior risk officer (Safeguarding officer) and to ensure compliance with the school policies.
The school believes that the activities referred to in the following section would be inappropriate in a school context and that users, as defined below, should not engage in these activities in / or outside the school when using school equipment or systems. The school policy restricts usage as follows:
| User Actions | Acceptable | Acceptable at certain times | Acceptable for nominated users | Unacceptable | Unacceptable and illegal | |
| Users shall not visit Internet sites, make, post, download, upload, data transfer, communicate or pass on, material, remarks, proposals or comments that contain or relate to: | Child sexual abuse images –The making, production or distribution of indecent images of children. Contrary to The Protection of Children Act 1978 | X | ||||
| Grooming, incitement, arrangement or facilitation of sexual acts against children Contrary to the Sexual Offences Act 2003. | X | |||||
| Possession of an extreme pornographic image (grossly offensive, disgusting or otherwise of an obscene character) Contrary to the Criminal Justice and Immigration Act 2008 | X | |||||
| Criminally racist material in UK – to stir up religious hatred (or hatred on the grounds of sexual orientation) – contrary to the Public Order Act 1986 | X | |||||
| Pornography | X | |||||
| Promotion of any kind of discrimination | X | |||||
| threatening behaviour, including promotion of physical violence or mental harm | X | |||||
| Promotion of extremism or terrorism | X | X | ||||
| Any other information which may be offensive to colleagues or breaches the integrity of the ethos of the school or brings the school into disrepute | X | |||||
| Using school systems to run a private business | X | |||||
| Using systems, applications, websites or other mechanisms that bypass the filtering or other safeguards employed by the school / academy | X | |||||
| Infringing copyright | X | |||||
| Revealing or publicising confidential or proprietary information (eg financial / personal information, databases, computer / network access codes and passwords) | X | |||||
| Creating or propagating computer viruses or other harmful files | X | |||||
| Unfair usage (downloading / uploading large files that hinders others in their use of the internet) | X | ||||
| On-line gaming (educational) | x | ||||
| On-line gaming (non-educational) | x | ||||
| On-line gambling | x | ||||
| On-line shopping / commerce | x | ||||
| File sharing | x | ||||
| Use of social media | x | ||||
| Use of messaging apps | x | ||||
| Use of video broadcasting e.g. YouTube | x |
If there is any suspicion that the web site(s) concerned may contain child abuse images, or if there is any other suspected illegal activity, refer to the right-hand side of the Flowchart (below and appendix) for responding to online safety incidents and report immediately to the police.
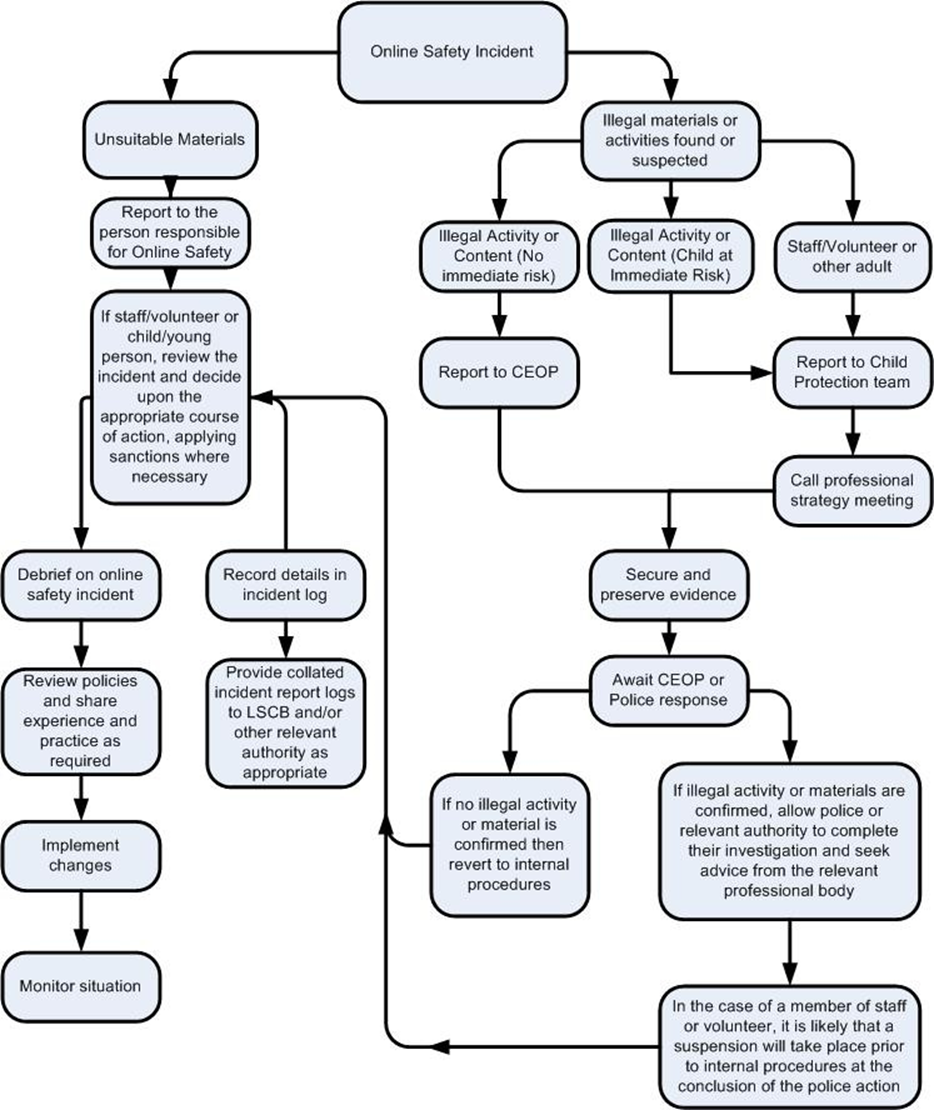
It is hoped that all members of the school community will be responsible users of digital technologies, who understand and follow school policy. However, there may be times when infringements of the policy could take place, through careless or irresponsible or, very rarely, through deliberate misuse.
In the event of suspicion, all steps in this procedure should be followed:
- Have more than one senior member of staff / volunteer involved in this process. This is vital to protect individuals if accusations are subsequently
- Conduct the procedure using a designated computer that will not be used by young people and if necessary, can be taken off site by the police should the need arise. Use the same computer for the duration of the
- It is important to ensure that the relevant staff should have appropriate internet access to conduct the procedure, but also that the sites and content visited are closely monitored and recorded (to provide further protection).
- Record the URL of any site containing the alleged misuse and describe the nature of the content causing concern. It may also be necessary to record and store screenshots of the content on the machine being used for investigation. These may be printed, signed and attached to the form (except in the case of images of child sexual abuse)
- Once this has been completed and fully investigated the group will need to judge whether this concern has substance or not. If it does then appropriate action will be required and could include the following:
- Internal response or discipline procedures
- Involvement by Local Authority Group or national / local organisation (as relevant).
- Police involvement and/or action
- If content being reviewed includes images of Child abuse, then the monitoring should be halted and referred to the Police immediately. Other instances to report to the police would include:
- incidents of ‘grooming’ behaviour
- the sending of obscene materials to a child
- adult material which potentially breaches the Obscene Publications Act
- criminally racist material
- promotion of terrorism or extremism
- other criminal conduct, activity or materials
- Isolate the computer in question as best you can. Any change to its state may hinder a later police investigation.
It is important that all of the above steps are taken as they will provide an evidence trail for the school and possibly the police and demonstrate that visits to these sites were carried out for safeguarding purposes. The completed form should be retained by the group for evidence and reference purposes.
Actions / Sanctions
|
Students / Pupils Incidents |
Refer to class teacher | Refer to Deputy Headteacher | Refer to Headteacher | Refer to Police | Refer to technical support staff for action re filtering / security etc. | Inform parents / carers | Removal of network / internet access rights | Warning | Further sanction e.g. detention / exclusion |
| Deliberately accessing or trying to access material that could be considered illegal (see list in earlier section on unsuitable / inappropriate activities). |
X |
X |
X |
X |
|||||
| Unauthorised use of non-educational sites during lessons |
X |
X |
|||||||
| Unauthorised / inappropriate use of mobile phone / digital camera / other mobile device |
X |
X |
|||||||
| Unauthorised / inappropriate use of social media / messaging apps / personal email |
X |
X |
X |
X |
X |
||||
| Unauthorised downloading or uploading of files | X | X | X | X | X | X | |||
| Allowing others to access school network by sharing username and passwords |
X |
X |
X |
X |
X |
||||
| Attempting to access or accessing the school network, using another student’s / pupil’s account |
X |
X |
|||||||
| Attempting to access or accessing the school | X | X | X |
| network, using the account of a member of staff | |||||||||
| Corrupting or destroying the data of other users | X | X | X | ||||||
| Sending an email, text or message that is regarded as offensive, harassment or of a bullying nature | X | X | X | X | X | X | X | ||
| Continued infringements of the above, following previous warnings or sanctions | X | ||||||||
| Actions which could bring the school / academy into disrepute or breach the integrity of the ethos of the school | X | X | X | ||||||
| Using proxy sites or other means to subvert the
school’s / academy’s filtering system |
X | X | X | X | X | ||||
| Accidentally accessing offensive or pornographic material and failing to report the incident | X | X | X | X | X | X | |||
| Deliberately accessing or trying to access offensive, dangerous or pornographic material | X | X | X | X | X | X | X | X | |
| Receipt or transmission of material that infringes the copyright of another person or infringes the Data Protection Act | X | X | X | X | X | X | X |
Actions / Sanctions
|
Staff Incidents |
Refer to Deputy Head | Refer to Headteacher | Refer to Local Authority | Refer to Police | Refer to Technical Support
Staff for action re filtering etc. |
Warning | Suspension | Disciplinary action |
| Deliberately accessing or trying to access material that could be considered illegal (see list in earlier section on unsuitable / inappropriate activities). |
X |
X |
X |
X |
||||
| Inappropriate personal use of the internet / social media / personal email |
X |
|||||||
| Unauthorised downloading or uploading of files | X |
| Allowing others to access school network by sharing username and passwords or attempting to access or accessing the school network, using another person’s account | X | X | ||||||
| Careless use of personal data e.g. holding or transferring data in an insecure manner | X | |||||||
| Deliberate actions to breach data protection or network security rules | X | |||||||
| Corrupting or destroying the data of other users or causing deliberate damage to hardware or software | X | |||||||
| Sending an email, text or message that is regarded as offensive, harassment or of a bullying nature | X | X | ||||||
| Using personal email / social networking / instant messaging / text messaging to carrying out digital communications with students / pupils | X | |||||||
| Actions which could compromise the staff member’s
professional standing |
X | |||||||
| Actions which could bring the school into disrepute or breach the integrity of the ethos of the school | X | |||||||
| Using proxy sites or other means to subvert the school’s
filtering system |
X | |||||||
| Accidentally accessing offensive or pornographic material and failing to report the incident | X | X | ||||||
| Deliberately accessing or trying to access offensive or pornographic material | X | X | ||||||
| Breaching copyright or licensing regulations | X | |||||||
| Continued infringements of the above, following previous warnings or sanctions | X |
ONLINESAFETYINCIDENTREPORTINGFORM
| Details of person reporting the incident Name:
Email address: |
| Date of incident: |
| Where did the incident take place? |
| Description of the incident |
| Name(s) of those involved in the incident: |
| Age(s) of child(ren) involved: |
| Was the incident
Child on child Child on adult Adult on child Adult on adult Staff member on child |
| Type of incident
Sexual Profanity Violence Bullying Grooming Radicalisation If Other, Please give details |
| How was the content accessed?
School internet via a PC/laptop via a table via a mobile phone via email Tablet using alternative provider mobile phone using an alternative provider Via an internet browser via a social media website via an app |
| What action was taken in relation to those involved in the incident? |
| What action was taken regarding the site/content accessed? |
| What follow-up action was taken?
Referral to LADO Referral to Children’s Social Care Advice to parents Police investigation Other Please provide details: |
STUDENT/ PUPILACCEPTABLEUSEPOLICYAGREEMENT– FORYOUNGERPUPILS(Foundation/ KS1)
This is how we stay safe when we use computers:
- I will ask a teacher or suitable adult if I want to use the computers / tablets
- I will only use activities that a teacher or suitable adult has told or allowed me to use
- I will take care of the computer and other equipment
- I will ask for help from a teacher or suitable adult if I am not sure what to do or if I think I have done something wrong
- I will tell a teacher or suitable adult if I see something that upsets me on the screen
- I know that if I break the rules, I might not be allowed to use a computer / tablet
Signed (child):
Signed (parent):
Digital technologies have become integral to the lives of children and young people, both within schools and outside school. These technologies provide powerful tools, which open up new opportunities for everyone. They can stimulate discussion, promote creativity and stimulate awareness of context to promote effective learning. Young people should have an entitlement to safe internet access at all times.
This Acceptable Use Policy is intended to ensure:
- that young people will be responsible users and stay safe while using the internet and other communications technologies for educational, personal and recreational
- that school / academy systems and users are protected from accidental or deliberate misuse that could put the security of the systems and users at
- that parents/carers are aware of the importance of online safety and are involved in the education and guidance of young people with regard to their on-line
The school will try to ensure that pupils will have good access to digital technologies to enhance their learning and will, in return, expect the pupils to agree to be responsible users. A copy of the Pupil Acceptable Use Policy is attached to this permission form, so that parents / carers will be aware of the school expectations of the young people in their care.
Parents are requested to sign the permission form below to show their support of the school in this important aspect of the school’s work.
Parent / Carer Permission Form
Parent / Carers Name:
Student / Pupil Name:
As the parent / carer of the above pupils, I give permission for my son / daughter to have access to the internet and to ICT systems at school.
Either: (KS2 and above)
I know that my son / daughter has signed an Acceptable Use Agreement and has received, or will receive, online safety education to help them understand the importance of safe use of technology and the internet – both in and out of school.
Or: (KS1)
I understand that the school has discussed the Acceptable Use Agreement with my son / daughter and that they have received, or will receive, online safety education to help them understand the importance of safe use of technology and the internet – both in and out of school.
I understand that the school will take every reasonable precaution, including monitoring and filtering systems, to ensure that young people will be safe when they use the internet and systems. I also understand that the school cannot ultimately be held responsible for the nature and content of materials accessed on the internet and using mobile technologies.
I understand that my son’s / daughter’s activity on the systems will be monitored and that the school will contact me if they have concerns about any possible breaches of the Acceptable Use Policy.
I will encourage my child to adopt safe use of the internet and digital technologies at home and will
inform the school if I have concerns over my child’s online safety.
Signed:
Date:
Images may also be used to celebrate success through their publication in newsletters, on the school website and occasionally in the public media.
The school will comply with the Data Protection Act and request parents / carers permission before taking images of members of the school. We will also ensure that when images are published that the young people cannot be identified by the use of their names.
In accordance with guidance from the Information Commissioner’s Office, parents / carers are welcome to take videos and digital images of their children at school events for their own personal use (as such use in not covered by the Data Protection Act). To respect everyone’s privacy and in some cases protection, these images should not be published / made publicly available on social networking sites, nor should parents / carers comment on any activities involving other pupils in the digital / video images.
Parents / carers are requested to sign the permission form to allow the school to take and use images of their children and for the parents / carers to agree.
Digital / Video Images Permission Form
Parent / Carers Name:
Student / Pupil Name:
| As the parent / carer of the above student / pupil, I agree to the school taking and using
digital / video images of my child / children. I understand that the images will only be used to support learning activities or in publicity that reasonably celebrates success and promotes the work of the school. |
Yes / No |
| I agree that if I take digital or video images at, or of – school events which include images
of children, other than my own, I will abide by these guidelines in my use of these images. |
Yes / No |
Signed:
Date:
KS: 2,3,4
Acceptable Use Policy Agreement
I understand that I must use school ICT systems in a responsible way, to ensure that there is no risk to my safety or to the safety and security of the ICT systems and other users.
For my own personal safety:
- I understand that the school will monitor my use of the systems, devices and digital communications.
- I will keep my username and password safe and secure – I will not share it, nor will I try to use any other person’s username and password. I understand that I should not write down or store a password where it is possible that someone may steal
- I will be aware of “stranger danger”, when I am communicating on-line.
- I will not disclose or share personal information about myself or others when on-line (this could include names, addresses, email addresses, telephone numbers, age, gender, educational details, financial details )
- If I arrange to meet people off-line that I have communicated with on-line, I will do so in a public place and take an adult with
- I will immediately report any unpleasant or inappropriate material or messages or anything that makes me feel uncomfortable when I see it on-line.
I understand that everyone has equal rights to use technology as a resource and:
- I understand that the school systems and devices are primarily intended for educational use and that I will not use them for personal or recreational use unless I have
- I will not try (unless I have permission) to make large downloads or uploads that might take up internet capacity and prevent other users from being able to carry out their
- I will not use the school systems or devices for on-line gaming, on-line gambling, internet shopping, file sharing, or video broadcasting (eg YouTube), unless I have permission of a member of staff to do so
I will act as I expect others to act toward me:
- I will respect others’ work and property and will not access, copy, remove or otherwise alter any other user’s files, without the owner’s knowledge and
- I will be polite and responsible when I communicate with others, I will not use strong, aggressive or inappropriate language and I appreciate that others may have different
- I will not take or distribute images of anyone without their
I recognise that the school has a responsibility to maintain the security and integrity of the technology it offers me and to ensure the smooth running of the school:
- I will only use my own personal devices (mobile phones / USB devices etc) in school if I have permission .I understand that, if I do use my own devices in the school, I will follow the rules set out in this agreement, in the same way as if I was using school
- I understand the risks and will not try to upload, download or access any materials which are illegal or inappropriate or may cause harm or distress to others, nor will I try to use any programmes or software that might allow me to bypass the filtering / security systems in place to prevent access to such
- I will immediately report any damage or faults involving equipment or software; however, this may have
- I will not open any hyperlinks in emails or any attachments to emails, unless I know and trust the person / organisation who sent the email, or if I have any concerns about the validity of the email (due to the risk of the attachment containing viruses or other harmful programmes)
- I will not install or attempt to install or store programmes of any type on any school device, nor will I try to alter computer
- I will only use social media sites with permission and at the times that are allowed
When using the internet for research or recreation, I recognise that:
- I should ensure that I have permission to use the original work of others in my own work
- Where work is protected by copyright, I will not try to download copies (including music and videos)
- When I am using the internet to find information, I should take care to check that the information that I access is accurate, as I understand that the work of others may not be truthful and may be a deliberate attempt to mislead
I understand that I am responsible for my actions, both in and out of school:
- I understand that the school also has the right to take action against me if I am involved in incidents of inappropriate behaviour, that are covered in this agreement, when I am out of school and where they involve my membership of the school community (examples would be cyber-bullying, use of images or personal information).
- I understand that if I fail to comply with this Acceptable Use Policy Agreement, I will be subject to disciplinary action. This may include loss of access to the school network / internet, detentions, suspensions, contact with parents and in the event of illegal activities involvement of the
Please complete the sections on the next page to show that you have read, understood and agree to the rules included in the Acceptable Use Agreement. If you do not sign and return this agreement, access will not be granted to school systems and devices.
Pupil Acceptable Use Agreement Form
This form relates to the pupil Acceptable Use Agreement, to which it is attached.
Please complete the sections below to show that you have read, understood and agree to the rules included in the Acceptable Use Agreement. If you do not sign and return this agreement, access will not be granted to school ICT systems.
I have read and understand the above and agree to follow these guidelines when:
- I use the school systems and devices (both in and out of school)
- I use my own devices in the school (when allowed) e.g. mobile phones, gaming devices USB devices, cameras etc
- I use my own equipment out of the school in a way that is related to me being a member of this school g. communicating with other members of the school, accessing school email, VLE, website etc.
Name of Pupil Group / Class Signed
Date
- School Policy
New technologies have become integral to the lives of children and young people in today’s society, both within schools and in their lives outside school. The internet and other digital information and communications technologies are powerful tools, which open up new opportunities for everyone. These technologies can stimulate discussion, promote creativity and stimulate awareness of context to promote effective learning. They also bring opportunities for staff to be more creative and productive in their work. All users should have an entitlement to safe access to the internet and digital technologies at all times.
This Acceptable Use Policy is intended to ensure:
- that staff and volunteers will be responsible users and stay safe while using the internet and other communications technologies for educational, personal and recreational
- that school systems and users are protected from accidental or deliberate misuse that could put the security of the systems and users at
- that staff are protected from potential risk in their use of technology in their everyday
The school will try to ensure that staff and volunteers will have good access to digital technology to enhance their work, to enhance learning opportunities for pupils learning and will, in return, expect staff and volunteers to agree to be responsible users.
2. Acceptable Use Policy Agreement
I understand that I must use school systems in a responsible way, to ensure that there is no risk to my safety or to the safety and security of the systems and other users. I recognise the value of the use of digital technology for enhancing learning and will ensure that students / pupils receive opportunities to gain from the use of digital technology. I will, where possible, educate the young people in my care in the safe use of digital technology and embed online safety in my work with young people.
For my professional and personal safety:
- I understand that the school will monitor my use of the school digital technology and communications
- I understand that the rules set out in this agreement also apply to use of these technologies (e.g. laptops, email, VLE etc.) out of school, and to the transfer of personal data (digital or paper based) out of school
- I understand that the school digital technology systems are primarily intended for educational use and that I will only use the systems for personal or recreational use within the policies and rules set down by the school. (Schools should amend this section in the light of their policies which relate to the personal use, by staff and volunteers, of school systems)
- I will not disclose my username or password to anyone else, nor will I try to use any other person’s username and password. I understand that I should not write down or store a password where it is possible that someone may steal
- I will immediately report any illegal, inappropriate or harmful material or incident, I become aware of, to the appropriate
I will be professional in my communications and actions when using school ICT systems:
- I will not access, copy, remove or otherwise alter any other user’s files, without their express permission.
- I will communicate with others in a professional manner, I will not use aggressive or inappropriate language and I appreciate that others may have different
- I will ensure that when I take and / or publish images of others I will do so with their
permission and in accordance with the school’s policy on the use of digital / video images. I will not use my personal equipment to record these images, unless I have permission to do so. Where these images are published (e.g. on the school website / VLE) it will not be possible to identify by name, or other personal information, those who are featured.
- I will only communicate with pupils and parents / carers using official school systems. Any such communication will be professional in tone and manner
- I will not engage in any on-line activity that may compromise my professional responsibilities.
The school and the local authority have the responsibility to provide safe and secure access to technologies and ensure the smooth running of the school:
- When I use my mobile devices (laptops / tablets / mobile phones / USB devices etc.) in school, I will follow the rules set out in this agreement, in the same way as if I was using school I will also follow any additional rules set by the school about such use. I will ensure that any such devices are protected by up-to-date anti-virus software and are free from viruses.
- I will not use personal email addresses on the school ICT systems unless permission
- I will not open any hyperlinks in emails or any attachments to emails, unless the source is known and trusted, or if I have any concerns about the validity of the email (due to the risk of the attachment containing viruses or other harmful programmes)
- I will ensure that my data is regularly backed up, in accordance with relevant school
- I will not try to upload, download or access any materials which are illegal (child sexual abuse images, criminally racist material, adult pornography covered by the Obscene Publications Act) or inappropriate or may cause harm or distress to others. I will not try to use any programmes or software that might allow me to bypass the filtering / security systems in place to prevent access to such
- I will not try (unless I have permission) to make large downloads or uploads that might take up internet capacity and prevent other users from being able to carry out their
- I will not install or attempt to install programmes of any type on a machine, or store programmes on a computer, nor will I try to alter computer settings, unless this is allowed in school
- I will not disable or cause any damage to school equipment, or the equipment belonging to others.
- I will only transport, hold, disclose or share personal information about myself or others, as outlined in the School LA Personal Data Policy (or other relevant policy). Where digital personal data is transferred outside the secure local network, it must be encrypted. Paper based Protected and restricted data must be held in lockable
- I understand that data protection policy requires that any staff or student / pupil data to which I have access, will be kept private and confidential, except when it is deemed necessary that I am required by law or by school policy to disclose such information to an appropriate
- I will immediately report any damage or faults involving equipment or software; however, this may have happened.
When using the internet in my professional capacity or for school sanctioned personal use:
- I will ensure that I have permission to use the original work of others in my own work
- Where work is protected by copyright, I will not download or distribute copies (including music and videos).
I understand that I am responsible for my actions in and out of the school:
- I understand that this Acceptable Use Policy applies not only to my work and use of school digital technology equipment in school, but also applies to my use of school systems and equipment off the premises and my use of personal equipment on the premises or in situations related to my employment by the school
- I understand that if I fail to comply with this Acceptable Use Policy Agreement, I could be subject to disciplinary action. This could include suspension or loss of job. A warning, a suspension, referral to Proprietor and the Local Authority and in the event of illegal activities the involvement of the
I have read and understand the above and agree to use the school digital technology systems (both in and out of school) and my own devices (in school and when carrying out communications related to the school) within these guidelines.
Staff / Volunteer Name:
Signed: Date: ………………………………
Recordofreviewing devices / internet sites (responding toincidentsofmisuse)
Group:
Date:
Reason for investigation:
Details of first reviewing person
Name:
Position:
Signature:
Details of second reviewing person
Name:
Position:
Signature:
Name and location of computer used for review (for web sites)
|
Web site(s) address / device |
Reason for concern |
Conclusion and Action proposed or taken
1. INTRODUCTION
Effective technical security depends not only on technical measures, but also on appropriate policies and procedures and on good user education and training. The school will be responsible for ensuring that the school infrastructure / network is as safe and secure as is reasonably possible and that:
- users can only access data to which they have right of access
- no user should be able to access another’s files (other than that allowed for monitoring purposes within the school’s policies).
- access to personal data is securely controlled in line with the school’s personal data policy
- logs are maintained of access by users and of their actions while users of the system
- there is effective guidance and training for users
- there are regular reviews and audits of the safety and security of school computer systems
- there is oversight from senior leaders and these have impact on policy and
2. RESPONSIBILITIES
The management of technical security will be the responsibility of the Headteacher Mr Gulam Hussain.
3. TECHNICAL SECURITY
3.1. Policy statements
The school will be responsible for ensuring that the school infrastructure / network is as safe and secure as is reasonably possible and that policies and procedures approved within this policy are implemented. It will also need to ensure that the relevant people receive guidance and training and will be effective in carrying out their responsibilities:
- School’s technical systems will be managed in ways that ensure that the it meets recommended technical requirements
- There will be regular reviews and audits of the safety and security of school technical systems
- Servers, wireless systems and cabling must be securely located and physical access restricted
- Appropriate security measures are in place to protect the servers, firewalls, switches, routers, wireless systems, work stations, mobile devices etc. from accidental or malicious attempts which might threaten the security of the school systems and
- Office doors are kept locked when not in use and supervised by a designated staff when
- Responsibilities for the management of technical security are clearly assigned to appropriate and well-trained staff
- All users will have clearly defined access rights to school technical systems. Details of the access rights available to groups of users will be recorded by the Network Manager Gulam
Hussain and will be reviewed, at least every two years or sooner, if necessary, by senior leadership team).
- Users will be made responsible for the security of their username and password must not allow other users to access the systems using their log on details and must immediately report any suspicion or evidence that there has been a breach of security. Mr Gulam Abbas Hussain is responsible for ensuring that software licence logs are accurate and up to date and that regular checks are made to reconcile the number of licences purchased against the number of software installations.
- The E- Safety officer will regularly monitor and record the activity of users on the school and users are made aware of this in the Acceptable Use
- An agreed decision will be made for the provision of temporary access of “guests” (e.g. trainee teachers, supply teachers, visitors) onto the school
- An agreed policy is in place regarding the downloading of executable files and the installation of programmes on school devices by users
- An agreed policy is in place regarding the extent of personal use that users (staff / pupils / community users) and their family members are allowed on school devices that may be used out of
- An agreed policy is in place regarding the use of removable media (e.g., memory sticks / CDs / DVDs) by users on school
- The school infrastructure and individual workstations are protected by up-to-date software to protect against malicious threats from viruses, worms, trojans etc
- Personal data cannot be sent over the internet or taken off the school site unless safely encrypted or otherwise
4. PASSWORD SECURITY
- Policy Statements
- All users will have clearly defined access rights to school technical systems and devices. Details of the access rights available to groups of users will be recorded by the Network Manager (or other person) and will be reviewed by the Online Safety Group (or another group).
- School networks and systems will be protected by secure passwords that are regularly changed
- The “master / administrator” passwords for the school systems, used by the technical staff must also be available to the Headteacher or other nominated senior leader and kept in a secure place e.g., school safe. Consideration should also be given to using two factor authentications for such accounts. This should never allow one user to have sole administrator access)
- All users (adults and young people) will have responsibility for the security of their username and password must not allow other users to access the systems using their log on details and must immediately report any suspicion or evidence that there has been a breach of
- Passwords for new users, and replacement passwords for existing users will be allocated by the office manager. Any changes carried out must be notified to the manager of the password security policy (above). Or:
- Passwords for new users and replacement passwords for existing users will be issued by the E-Safety Officer or a senior leader on behalf of the E-Safety
- Where passwords are set / changed manually requests for password changes should be authenticated by the E-safety Officer to ensure that the new password can only be passed to the genuine user and authorised by a line manager for a request by a member of staff or by a member of staff for a request by a
4.2. STAFF/ PUPIL PASSWORDS
- All staff users will be provided with a username and password who / which will keep an up- to-date record of users and their
- the password should be a minimum of 8 characters long and must include three of –
uppercase character, lowercase character, number, special characters
- must not include proper names or any other personal information about the user that might be known by others
- the account should be “locked out” following six successive incorrect log-on attempts
- temporary passwords e.g. used with new user accounts or when users have forgotten their passwords, shall be enforced to change immediately upon the next account log-on
- passwords shall not be displayed on screen, and shall be securely hashed (use of one-way encryption)
- passwords should be different for different accounts, to ensure that other systems are not put at risk if one is compromised and should be different for systems used inside and outside of school
- When required users (at KS2 and above) will be provided with a username and password
- Users will be advised to change their passwords when deemed
- Pupils will be taught the importance of password
4.3. Training / Awareness
It is essential that users should be made aware of the need for keeping passwords secure, and the risks attached to unauthorised access / data loss. This should apply to even the youngest of users, even if class log-ins are being used.
Members of staff will be made aware of the school’s password procedure:
- at induction
- through the school’s online safety policy
- through the Acceptable Use Agreement
Pupils will be made aware of the school’s password policy:
- in lessons
- through the Acceptable Use Agreement
4.4. Audit / Monitoring / Reporting / Review
The responsible person (Mr Gulam Abbas Hussain) will ensure that full records are kept of:
- User Ids and requests for password changes
- User log-ins
- Security incidents related to this policy
5. FILTERING
- Introduction
The filtering of internet content provides an important means of preventing users from accessing material that is illegal or is inappropriate in an educational context. The filtering system cannot, however, provide a 100% guarantee that it will do so, because the content on the web changes dynamically and new technologies are constantly being developed. It is important, therefore, to understand that filtering is only one element in a larger strategy for online safety and acceptable use. It is important that the school has a filtering policy to manage the associated risks and to provide preventative measures which are relevant to the situation in this school.
5.2. Responsibilities
The responsibility for the management of the school’s filtering policy will be held by the Head teacher. They will manage the school filtering, in line with this policy and will keep records / logs of changes and of breaches of the filtering systems.
To ensure that there is a system of checks and balances and to protect those responsible, changes to the school filtering service must
Be connected to up-to-date security system
- Be reported to a second responsible person
All users have a responsibility to report immediately to the headteacher any infringements of the school’s filtering policy of which they become aware or any sites that are accessed, which they believe should have been filtered.
Users must not attempt to use any programmes or software that might allow them to bypass the filtering / security systems in place to prevent access to such materials.
5.3. Policy Statements
Internet access is filtered for all users. Differentiated internet access is available for staff and customised filtering changes are managed by the school. Illegal content is filtered by the broadband or filtering provider by actively employing the Internet Watch Foundation CAIC list and other illegal content lists. Filter content lists are regularly updated and internet use is logged and frequently monitored. The monitoring process alerts the school to breaches of the filtering policy, which are then acted upon. There is a clear route for reporting and managing changes to the filtering system. Where personal mobile devices are allowed internet access through the school network, filtering will be applied that is consistent with school practice.
- Mobile devices that access the school’s connection will be subject to the same filtering standards as other devices on the school systems
- Requests from staff for sites to be removed from the filtered list will be considered by the headteacher and technical staff (If the request is agreed, this action will be recorded and logs of such actions shall be reviewed regularly by the E- safety team)
5.4. Education / Training / Awareness
Pupils will be made aware of the importance of filtering systems through the online safety education programme held during safety week. They will also be warned of the consequences of attempting to subvert the filtering system.
Staff users will be made aware of the filtering systems through:
- the Acceptable Use Agreement
- induction training
- staff meetings, briefings,
Parents will be informed of the school’s filtering policy through the Acceptable Use Agreement and
through online safety awareness sessions / newsletter etc.
5.5. Changes to the Filtering System
In this section the school should provide a detailed explanation of:
- how, and to whom, users may request changes to the filtering (whether this is carried out in school or by an external filtering provider)
- the grounds on which they may be allowed or denied (schools may choose to allow access to some sites e.g. social networking sites for some users, at some times, or for a limited period of time. There should be strong educational reasons for changes that are agreed).
- how a second responsible person will be involved to provide checks and balances (preferably this will be at the time of request, but could be retrospectively through inspection of records / audit of logs)
- any audit / reporting system
Users who gain access to, or have knowledge of others being able to access, sites which they feel should be filtered (or unfiltered) should report this in the first instance to Mr Gulam Abbas Hussain who will decide whether to make school level changes (as above).
6. MONITORING
The schools supplement their filtering systems with additional monitoring by Proprietor regularly. No filtering system can guarantee 100% protection against access to unsuitable sites. The school will therefore monitor the activities of users on the school network and on school equipment as indicated in the School Online Safety Policy and the Acceptable Use Agreement.
Audit / Reporting
Logs of filtering change controls and of filtering incidents will be made available to the Headteacher.
Schools in England (and Wales) are required “to ensure children are safe from terrorist and extremist material when accessing the internet in school, including by establishing appropriate levels of filtering” (Revised Prevent Duty Guidance: for England and Wales, 2015).
Furthermore the Department for Education published that schools will be obligated to “ensure appropriate filters and appropriate monitoring systems are in place. Children should not be able to access harmful or inappropriate material from the school or colleges IT system” however, schools will need to “be careful that “over blocking” does not lead to unreasonable restrictions as to what children can be taught with regards to online teaching and safeguarding.”
- INTRODUCTION
At Read Academy all employees should do everything within their power to ensure the safety and security of any material of a personal or sensitive nature
It is the responsibility of all members of the school community to take care when handling, using or transferring personal data that it cannot be accessed by anyone who does not:
- have permission to access that data, and/or
- Need to have access to that
Data breaches can have serious effects on individuals and / or institutions concerned, can bring the school into disrepute and may well result in disciplinary action, criminal prosecution and fines imposed by the Information Commissioners Office. For the school and the individuals involved.
Particularly, all transfer of data is subject to risk of loss or contamination.
Anyone who has access to personal data must know, understand and adhere to this policy, which brings together the legal requirements contained in relevant data protection legislation and relevant regulations and guidance (where relevant from the Local Authority).
2. POLICY STATEMENTS
The school will hold the minimum personal data necessary to enable it to perform its function and it will not hold it for longer than necessary for the purposes it was collected for.
Every effort will be made to ensure that data held is accurate, up to date and that inaccuracies are corrected without unnecessary delay.
All personal data will be fairly obtained in accordance with the “Privacy Notice” and lawfully processed in accordance with the “Conditions for Processing”.
PERSONAL DATA
The school and individuals will have access to a wide range of personal information and data. The data may be held in a digital format or on paper records. Personal data is defined as any combination of data items that identifies an individual and provides specific information about them, their families or circumstances. This will include:
- Personal information about members of the school community – including pupils / students, members of staff and parents / carers e.g. names, addresses, contact details, legal guardianship contact details, health records, disciplinary records
- Curricular / academic data e.g. class lists, pupil / student progress records, reports, references
- Professional records e.g. employment history, taxation and national insurance records, appraisal records and references
- Any other information that might be disclosed by parents / carers or by other agencies working with families or staff
2.1. Responsibilities
The school’s safeguarding Officers; will keep up to date with current legislation and guidance and will:
- determine and take responsibility for the school’s information risk policy and risk assessment
Everyone in the school has the responsibility of handling protected or sensitive data in a safe and secure manner.
Proprietors are required to comply fully with this policy in the event that they have access to personal data, when engaged in their role as a SDL.
Registration
The school is registered as a Data Controller on the Data Protection Register held by the Information Commissioner. (each school is responsible for their own registration): http://www.ico.gov.uk/what_we_cover/register_of_data_controllers.aspx
2.2. Information to Parents / Carers – the “Privacy Notice”
In order to comply with the fair processing requirements of the DPA, the school will inform parents / carers of all of the data they collect, process and hold on the pupils, the purposes for which the data is held and the third parties (e.g. LA, DfE, etc) to whom it may be passed. This privacy notice will be passed to parents / carers through Prospectus, newsletters, reports or a specific letter / communication). Parents / carers of young people who are new to the school will be provided with the privacy notice through them.
More information about the suggested wording of privacy notices can be found on the DfE website:
2.3. Training & Awareness
All staff will receive data handling awareness / data protection training and will be made aware of their responsibilities, as described in this policy through: Induction training for new staff
- Staff meetings / briefings / Inset
- Day to day support and guidance from Information Asset Owners
2.4. Impact Levels and protective marking
Following incidents involving loss of data, the Government recommends that the Protective Marking Scheme should be used to indicate the sensitivity of data. The Protective Marking Scheme is mapped to Impact Levels as follows:
| Government Protective Marking Scheme label | Impact Level (IL) | Applies to schools? |
| Not Protectively Marked | 0 | Will apply in schools |
| Protect | 1 or 2 | |
| Restricted | 3 | |
| Confidential | 4 | Will not apply in schools |
| Highly Confidential | 5 | |
| Top Secret | 6 |
Most pupil or staff personal data that is used within educational institutions will come under the PROTECT classification. However, some, e.g. the home address of a child (or vulnerable adult) at risk will be marked as RESTRICT.
The school will ensure that all school staff, independent contractors working for it, and delivery partners, comply with restrictions applying to the access to, handling and storage of data classified as Protect, Restricted or higher. Unmarked material is considered ‘unclassified’. The term
‘UNCLASSIFIED’ or ‘NON‘ or ‘NOT PROTECTIVELY MARKED’ may be used to indicate positively that a protective marking is not needed.
All documents (manual or digital) that contain protected or restricted data will be labelled clearly with the Impact Level shown in the header and the Release and Destruction classification in the footer.
Users must be aware that when data is aggregated the subsequent impact level may be higher than the individual impact levels of the original data. Combining more and more individual data elements together in a report or data view increases the impact of a breach. A breach that puts pupils at serious risk of harm will have a higher impact than a risk that puts them at low risk of harm. Long-
term significant damage to anyone’s reputation has a higher impact than damage that might cause short-term embarrassment.
Release and destruction markings should be shown in the footer e.g. “Securely delete or shred this information when you have finished using it”.
2.5. Secure Storage of and access to data
The school will ensure that systems are set up so that the existence of protected files is hidden from unauthorised users and that users will be assigned a clearance that will determine which files are accessible to them. Access to protected data will be controlled according to the role of the user.
Members of staff will not, as a matter of course, be granted access to the whole management information system.
All users will use strong passwords which will be changed regularly. User passwords must never be shared.
Personal data may only be accessed on machines that are securely password protected. Any device that can be used to access data must be locked if left (even for very short periods) and set to auto lock if not used for five minutes.
All storage media must be stored in an appropriately secure and safe environment that avoids physical risk, loss or electronic degradation.
When personal data is stored on any portable computer system or any other removable media:
- the data must be encrypted and password protected,
- the device must be password protected (many memory sticks / cards and other mobile devices cannot be password protected therefore the school will not allow such
- the device must offer approved virus and malware checking software (and
- the data must be securely deleted from the device, in line with school policy (below) once it has been transferred or its use is
The school will not allow storage of personal data on removable devices.
The school has clear policy and procedures for the automatic backing up, accessing and restoring all data held on school systems, including off-site backups.
The school has clear policy and procedures for the use of “Cloud Based Storage Systems” (for example drop box, Microsoft 365, google apps and google docs) and is aware that data held in remote and cloud storage is still required to be protected in line with the Data Protection Act. The school will ensure that it is satisfied with controls put in place by remote / cloud-based data services providers to protect the data.
(see appendix for further information and the ICO Guidance: http://www.ico.org.uk/for_organisations/guidance_index/~/media/documents/library/Data_Protect ion/Practical_application/cloud_computing_guidance_for_organisations.ashx
As a Data Controller, the school is responsible for the security of any data passed to a “third party”. Data Protection clauses will be included in all contracts where data is likely to be passed to a third party. All paper based Protected and Restricted (or higher) material must be held in lockable storage, whether on or off site.
2.6. Secure transfer of data and access out of school
The school recognises that personal data may be accessed by users out of school, or transferred to the LA or other agencies. In these circumstances:
- Users may not remove or copy sensitive or restricted or protected personal data from the school or authorised premises without permission and unless the media is encrypted and password protected and is transported securely for storage in a secure location. The school is signed on to egress for transfer of any confidential materials/information.
- Users must take particular care that computers or removable devices which contain personal data must not be accessed by other users (e.g. family members) when out of school
- When restricted or protected personal data is required by an authorised user from outside the organisation’s premises (for example, by a member of staff to work from their home), they should preferably have secure remote access to the management information system or learning platform;
- If secure remote access is not possible, users must only remove or copy personal or sensitive data from the organisation or authorised premises if the storage media, portable or mobile device is encrypted and is transported securely for storage in a secure location;
- Users must protect all portable and mobile devices, including media, used to store and transmit personal information using approved encryption software; and
- Particular care should be taken if data is taken or transferred to another country, particularly outside Europe, and advice should be taken from the local authority (if relevant) in this event.
2.7. Disposal of data
The school will comply with the requirements for the safe destruction of personal data when it is no longer required. The disposal of personal data, in either paper or electronic form, must be conducted in a way that makes reconstruction highly unlikely. Electronic files must be securely overwritten, in accordance with government guidance and other media must be shredded, incinerated or otherwise disintegrated for data.
3. USE OF TECHNOLOGIES AND PROTECTIVE MARKING
The following provides a useful guide:
| The information | The technology | Notes on Protect Markings
(Impact Level) |
|
| School life and events | School terms, holidays, training days, the curriculum, extra- curricular activities, events, displays of pupils work, lunchtime menus, extended services, parent
consultation events |
Common practice is to use publicly accessible technology such as school websites or portal, emailed newsletters, subscription text
services |
Most of this information will fall into the NOT PROTECTIVELY MARKED
(Impact Level 0) category. |
| Individual pupil / student | Typically, schools will | Most of this information | |
| academic, social and | make information | will fall into the PROTECT | |
| behavioural | available by parents | (Impact Level 2) category. | |
| achievements, progress | logging on to a system | There may be students/ | |
| with learning, learning | that provides them with | pupils whose personal data | |
| Learning and | behaviour, how parents | appropriately secure | requires a RESTRICTED |
| achievement | can support their child’s | access, such as a | marking (Impact Level 3) or |
| learning, assessments, | Learning Platform or | higher. For example, the | |
| attainment, attendance, | portal, or by | home address of a child at | |
| individual and | communication to a | risk. In this case, the school | |
| personalised curriculum | personal device or email | may decide not to make this | |
| and educational needs. | account belonging to | pupil / student record | |
| the parent. | available in this way. | ||
| Attendance, behavioural, | Email and text | Most of this information | |
| achievement, sickness, | messaging are | will fall into the PROTECT | |
| school closure, transport | commonly used by | (Impact Level 1) category. | |
| arrangements, and other | schools to contact and | However, since it is not | |
| information that it may | keep parents informed. | practical to encrypt email or | |
| be important to inform or | Where parents are | text messages to parents, | |
| Messages and alerts | contact a parent about as soon as possible. This
may be particularly |
frequently accessing information online then
systems e.g. Learning |
schools should not send detailed personally
identifiable information. |
| important when it is | Platforms or portals, | General, anonymous alerts | |
| necessary to contact a | might be used to alert | about schools’ closures or | |
| parent concerning | parents to issues via | transport arrangements | |
| information that may be | “dashboards” of | would fall into the NOT | |
| considered too sensitive | information, or be used | PROTECTIVELY MARKED | |
| to make available using | to provide further detail | (Impact Level 0) category. | |
| other online means. | and context. |
- INTRODUCTION
The changing face of information technologies and ever-increasing pupil use of these technologies has meant that the Education Acts have had to change in an attempt to keep pace. Within Part 2 of the Education Act 2011 (Discipline) there have been changes to the powers afforded to schools by statute to search pupils in order to maintain discipline and ensure safety. Schools are required to ensure they have updated policies which take these changes into account. No such policy can on its own guarantee that the school will not face legal challenge, but having a robust policy which takes account of the Act and applying it in practice will however help to provide the school with justification for what it does.
The particular changes we deal with here are the added power to search for items ‘banned under
the school rules’ and the power to ‘delete data’ stored on seized electronic devices.
Items banned under the school rules are determined and publicised by the Headteacher (section 89 Education and Inspections Act 1996).
An item banned by the school rules may only be searched for under these new powers if it has been identified in the school rules as an item that can be searched for. It is therefore important that there is a school policy which sets out clearly and unambiguously the items which:
- are banned under the school rules; and
- are banned AND can be searched for by authorised school staff
The act allows authorised persons to examine data on electronic devices if they think there is a good reason to do so. In determining a ‘good reason’ to examine or erase the data or files the authorised staff member must reasonably suspect that the data or file on the device in question has been, or could be, used to cause harm, to disrupt teaching or could break the school rules.
Following an examination, if the person has decided to return the device to the owner, or to retain or dispose of it, they may erase any data or files, if they think there is a good reason to do so.
It is recommended that Headteacher (and, at the least, other senior leaders) should be familiar with guidance on searching and deletion.
2. RESPONSIBILITIES
The Headteacher is responsible for ensuring that the school policies reflect the requirements contained within the relevant legislation. The formulation of these policies may be delegated to other individuals or groups. The policies will normally be taken to Proprietor/s for approval. The Headteacher will need to authorise those staff who are allowed to carry out searches.
This policy has been written by and will be reviewed by: Mr Gulam Abbas Hussain
The Headteacher has authorised the following members of staff to carry out searches for and of electronic devices and the deletion of data / files on those devices: Hanila Ali Syed & Farhana Begum.
The Headteacher may authorise other staff members in writing in advance of any search they may undertake, subject to appropriate training.
3. TRAINING / AWARENESS
Members of staff should be made aware of the school’s policy on “Electronic devices – searching and deletion”:
- at induction
- at regular updating sessions on the school’s online safety policy
Members of staff authorised by the Headteacher to carry out searches for and of electronic devices and to access and delete data / files from those devices should receive training that is specific and relevant to this role. Specific training is required for those staff who may need to judge whether material that is accessed is inappropriate or illegal.
4. POLICYSTATEMENTS
- Electronic devices
An authorised member of staff finding an electronic device may access and examine any data or files on the device if they think there is a good reason to do so (i.e. the staff member must reasonably suspect that the data or file on the device in question has been, or could be, used to cause harm, to disrupt teaching or break the school rules).
The examination of the data / files on the device should go only as far as is reasonably necessary to establish the facts of the incident. Any further intrusive examination of personal data may leave the school open to legal challenge. It is important that authorised staff should have training and sufficient knowledge of electronic devices and data storage.
If inappropriate material is found on the device it is up to the authorised member of staff to decide whether they should delete that material, retain it as evidence (of a criminal offence or a breach of school discipline) or whether the material is of such seriousness that it requires the involvement of the police. Examples of illegal activity would include:
child sexual abuse images (including images of one child held by another child)
- adult material which potentially breaches the Obscene Publications Act
- criminally racist material
- other criminal conduct, activity or materials
Members of staff may require support in judging whether the material is inappropriate or illegal. One or more Senior Leaders should receive additional training to assist with these decisions. Care should be taken not to delete material that might be required in a potential criminal investigation.
The school should also consider their duty of care responsibility in relation to those staff who may access disturbing images or other inappropriate material whilst undertaking a search. Seeing such material can be most upsetting. There should be arrangements in place to support such staff.
Further guidance on reporting the incident to the police and the preservation of evidence can be found with Local authorities / LSCBs may also have further guidance.
7.2. Deletion of Data
Following an examination of an electronic device, if the authorised member of staff has decided to return the device to the owner, or to retain or dispose of it, they may erase any data or files, if they think there is a good reason to do so. (i.e. the staff member must reasonably suspect that the data or file on the device in question has been, or could be, used to cause harm, to disrupt teaching or break the school rules).
If inappropriate material is found on the device, it is up to the authorised member of staff to decide whether they should delete that material, retain it as evidence (of a possible criminal offence or a breach of school discipline) or whether the material is of such seriousness that it requires the involvement of the police.
A record should be kept of the reasons for the deletion of data / files. (DfE guidance states and other legal advice recommends that there is no legal reason to do this, best practice suggests that the school can refer to relevant documentation created at the time of any search or data deletion in the event of a pupil, parental or other interested party complaint or legal challenge. Records will also help the school to review online safety incidents, learn from what has happened and adapt and report on application of policies as necessary).
7.3. Care of Confiscated Devices
School staff are reminded of the need to ensure the safe keeping of confiscated devices, to avoid the risk of compensation claims for damage / loss of such devices (particularly given the possible high value of some of these devices).
5. AUDIT / MONITORING / REPORTING / REVIEW
The responsible person Mr Gulam Abbas Hussain will ensure that full records are kept of incidents involving the searching for and of mobile phones and electronic devices and the deletion of data / files.
This policy will be reviewed by the head teacher and governors every two years or soon if necessary and in response to changes in guidance and evidence gained from the records.
Mobile Technologies Policy
Mobile technology devices may be a school owned/provided or privately-owned smartphone, tablet, notebook / laptop or other technology that usually has the capability of utilising the school’s wireless network. The device then has access to the wider internet which may include the school’s learning platform and other cloud-based services such as email and data storage.
The absolute key to considering the use of mobile technologies is that the pupils, staff and wider school community understand that the primary purpose of having their personal device at school is educational and that this is irrespective of whether the device is school owned/provided or personally owned. Further information can be found in the school’s BYOD (bring your own device) policy.
6. POTENTIAL BENEFITS OF MOBILE TECHNOLOGIES
Research has highlighted the widespread uptake of mobile technologies amongst adults and children of all ages. Web-based tools and resources have changed the landscape of learning. pupils now have at their fingertips unlimited access to digital content, resources, experts, databases and communities of interest. By effectively maximizing the use of such resources, schools not only have the opportunity to deepen student learning, but they can also develop digital literacy, fluency and citizenship in pupils that will prepare them for the high-tech world in which they will live, learn and work.
9.1. Considerations
There are a number of issues and risks to consider when implementing mobile technologies, these include; security risks in allowing connections to your school network, filtering of personal devices, breakages and insurance, access to devices for all pupils, avoiding potential classroom distraction, network connection speeds, types of devices, charging facilities, total cost of ownership etc.
Schools may consider implementing the use of mobile technologies as a means of reducing expenditure on school provided devices. However, it is important to remember that the increased network management costs and overheads involved in implementing this properly are likely to counterbalance or outweigh any savings.
The use of mobile technologies brings both real benefits and challenges for the whole school community – including teachers – and the only effective way for a school to implement these successfully is to involve the whole school community from the outset. Before the school embarks on this path, the risks and benefits must be clearly identified and shared with all stakeholders.
- The school Acceptable Use Agreements for staff, pupils and parents/carers will give consideration to the use of mobile
- The school allows:
| School Devices | Personal Devices | |||||
| School owned and allocated to a single user | School owned for use by multiple
users |
Authorised device1 | Pupil owned | Staff owned | Visitor owned | |
| Allowed in
school |
Yes | Yes | Yes | No2 | Yes | Yes |
| Full network
access |
Yes | Yes | Yes | |||
| Internet only | Yes | |||||
| No network
access |
Yes | |||||
- The school has provided technical solutions for the safe use of mobile technology for school devices/personal devices (delete / amend as appropriate):
- All school devices are controlled though the use of Mobile Device Management software
- Appropriate access control is applied to all mobile devices according to the requirements of the user (e.g. Internet only access, network access allowed, shared folder network access)
1Authorised device – purchased by the pupil/family through a school-organised scheme. This device may be given full access to the network as if it were owned by the school
2The school should add below any specific requirements about the use of personal devices in school,
e.g. storing in a secure location, use during the school day, liability, taking images etc.
- The school has addressed broadband performance and capacity to ensure that core educational and administrative activities are not negatively affected by the increase in the number of connected devices
- For all mobile technologies, filtering will be applied to the internet connection and attempts to bypass this are not permitted
- Appropriate exit processes are implemented for devices no longer used at a school location or by an authorised user
- All school devices are subject to routine monitoring
- Pro-active monitoring has been implemented to monitor activity
When personal devices are permitted:
- All personal devices are restricted through the implementation of technical solutions that provide appropriate levels of network access
- Personal devices are brought into the school entirely at the risk of the owner and the decision to bring the device in to the school lies with the user (and their parents/carers) as does the liability for any loss or damage resulting from the use of the device in school
- The school accepts no responsibility or liability in respect of lost, stolen or damaged devices while at school or on activities organised or undertaken by the school (the school recommends insurance is purchased to cover that device whilst out of the home)
- The school accepts no responsibility for any malfunction of a device due to changes made to the device while on the school network or whilst resolving any connectivity issues
- The school recommends that the devices are made easily identifiable and have a protective case to help secure them as the devices are moved around the Pass-codes or PINs should be set on personal devices to aid security
- The school is not responsible for the day-to-day maintenance or upkeep of the user’s personal device such as the charging of any device, the installation of software updates or the resolution of hardware issues
Users are expected to act responsibly, safely and respectfully in line with current Acceptable Use Agreements, in addition;
- Devices may not be used in tests or exams
- Visitors should be provided with information about how and when they are permitted to use mobile technology in line with local safeguarding arrangements
- Users are responsible for keeping their device up to date through software, security and app updates. The device is virus protected and should not be capable of passing on infections to the network
- Users are responsible for charging their own devices and for protecting and looking after their devices while in school
- Personal devices should be charged before being brought to school as the charging of personal devices is not permitted during the school day
- Devices must be in silent mode on the school
- School devices are provided to support learning. It is expected that pupils will bring devices to school as required.
- Confiscation and searching (England) – the school has the right to take, examine and search any device that is suspected of unauthorised use, either technical or inappropriate.
- The changing of settings (exceptions include personal settings such as font size, brightness, etc.…) that would stop the device working as it was originally set up and intended to work is not permitted
- The software / apps originally installed by the school must remain on the school owned device in usable condition and be easily accessible at all times. From time to time the school may add software applications for use in a particular lesson. Periodic checks of devices will be made to ensure that users have not removed required apps
- The school will ensure that school devices contain the necessary apps for school work. Apps added by the school will remain the property of the school and will not be accessible to pupils on authorised devices once they leave the school roll. Any apps bought by the user on their own account will remain
- Users should be mindful of the age limits for app purchases and use and should ensure they read the terms and conditions before
- Users must only photograph people with their permission. Users must only take pictures or videos that are required for a task or activity. All unnecessary images or videos will be deleted immediately
- Devices may be used in lessons in accordance with teacher direction
- Staff owned devices should not be used for personal purposes during teaching sessions, unless in exceptional circumstances
- Printing from personal devices will not be possible
Social media (e.g. Facebook, Twitter, LinkedIn) is a broad term for any kind of online platform which enables people to directly interact with each other. However, some games, for example Minecraft or World of Warcraft and video sharing platforms such as You Tube have social media elements to them.
The school recognises the numerous benefits and opportunities which a social media presence offers. Staff, parents/carers and pupils are actively encouraged to find creative ways to use social media. However, there are some risks associated with social media use, especially around the issues of safeguarding, bullying and personal reputation. This policy aims to encourage the safe use of social media by the school, its staff, parents, carers and children.
1. SCOPE
This policy is subject to the school’s Codes of Conduct and Acceptable Use Agreements.
This policy:
- Applies to all staff and to all online communications which directly or indirectly, represent the school.
- Applies to such online communications posted at any time and from
- Encourages the safe and responsible use of social media through training and education
- Defines the monitoring of public social media activity pertaining to the school
The school respects privacy and understands that staff and pupils may use social media forums in their private lives. However, personal communications likely to have a negative impact on
professional standards and/or the school’s reputation are within the scope of this policy.
Professional communications are those made through official channels, posted on a school account or using the school name. All professional communications are within the scope of this policy.
Personal communications are those made via a personal social media account. In all cases, where a personal account is used which associates itself with the school or impacts on the school, it must be made clear that the member of staff is not communicating on behalf of the school with an appropriate disclaimer. Such personal communications are within the scope of this policy.
Personal communications which do not refer to or impact upon the school are outside the scope of this policy.
Digital communications with pupils are also considered. Staff may use social media to communicate with learners via a school social media account for teaching and learning purposes but must consider whether this is appropriate and consider the potential implications.
2. ORGANISATIONAL CONTROL
- Roles & Responsibilities
2.1.1. SLT
- Facilitating training and guidance on Social Media
- Developing and implementing the Social Media policy
- Taking a lead role in investigating any reported
- Making an initial assessment when an incident is reported and involving appropriate staff and external agencies as
- Receive completed applications for Social Media accounts
- Approve account creation
2.1.2. Administrator
- Create the account following SLT approval
- Store account details, including passwords securely
- Be involved in monitoring and contributing to the account
- Control the process for managing an account after the lead staff member has left the organisation (closing or transferring)
2.1.3. Staff
- Know the contents of and ensure that any use of social media is carried out in line with this and other relevant policies
- Attending appropriate training
- Regularly monitoring, updating and managing content he/she has posted via school accounts
- Adding an appropriate disclaimer to personal accounts when naming the school
2.2. Process for creating new accounts
The school community is encouraged to consider if a social media account will help them in their work, e.g. a history department Twitter account, or a “Friends of the school” Facebook page.
Anyone wishing to create such an account must present a business case to the School Leadership Team which covers the following points: –
- The aim of the account
- The intended audience
- How the account will be promoted
- Who will run the account (at least two staff members should be named)
- Will the account be open or private/closed?
Following consideration by the SLT, an application will be approved or rejected. In all cases, the SLT must be satisfied that anyone running a social media account on behalf of the school has read and understood this policy and received appropriate training. This also applies to anyone who is not directly employed by the school, including volunteers or parents.
- Monitoring
School accounts must be monitored regularly and frequently. Any comments, queries or complaints made through those accounts must be responded to within 24 hours (or on the next working day if received at a weekend) even if the response is only to acknowledge receipt. Regular monitoring and intervention are essential in case a situation arises where bullying or any other inappropriate behaviour arises on a school social media account.
- Behaviour
- The school requires that all users using social media adhere to the standard of behaviour as set out in this policy and other relevant
- Digital communications by staff must be professional and respectful at all times and in accordance with this policy.
- Staff will not use social media to infringe on the rights and privacy of others or make ill- considered comments or judgments about staff. School social media accounts must not be used for personal gain. Staff must ensure that confidentiality is maintained on social media even after they leave the employment of the
- Users must declare who they are in social media posts or accounts. Anonymous posts are discouraged in relation to school
- If a journalist makes contact about posts made using social media staff must follow the school media policy before
- Unacceptable conduct, (e.g. defamatory, discriminatory, offensive, harassing content or a breach of data protection, confidentiality, copyright) will be considered extremely seriously by the school and will be reported as soon as possible to a relevant senior member of staff, and escalated where
- The use of social media by staff while at work may be monitored, in line with school policies. The school permits reasonable and appropriate access to private social media sites. However, where excessive use is suspected, and considered to be interfering with relevant duties, disciplinary action may be
- The school will take appropriate action in the event of breaches of the social media policy. Where conduct is found to be unacceptable, the school will deal with the matter internally. Where conduct is considered illegal, the school will report the matter to the police and other relevant external agencies, and may take action according to the disciplinary
- Legal considerations
- Users of social media should consider the copyright of the content they are sharing and, where necessary, should seek permission from the copyright holder before
- Users must ensure that their use of social media does not infringe upon relevant data protection laws, or breach
- Handling abuse
- When acting on behalf of the school, handle offensive comments swiftly and with
- If a conversation turns and becomes offensive or unacceptable, school users should block, report or delete other users or their comments/posts and should inform the audience exactly why the action was
- If you feel that you or someone else is subject to abuse by colleagues through use of a social networking site, then this action must be reported using the agreed school
- Tone
The tone of content published on social media should be appropriate to the audience, whilst retaining appropriate levels of professional standards. Key words to consider when composing messages are:
- Engaging
- Conversational
- Informative
- Friendly (on certain platforms, e.g. Facebook)
3. USE OF IMAGES
School use of images can be assumed to be acceptable, providing the following guidelines are strictly adhered to.
- Permission to use any photos or video recordings should be sought in line with the school’s digital and video images policy. If anyone, for any reason, asks not to be filmed or photographed then their wishes should be
Under no circumstances should staff share or upload pupil’s pictures online other than via school owned social media accounts.
- Staff should exercise their professional judgement about whether an image is appropriate to share on school social media accounts. Pupils should be appropriately dressed, not be subject to ridicule and must not be on any school list of children whose images must not be published.
- If a member of staff inadvertently takes a compromising picture which could be misconstrued or misused, they must delete it
4. PERSONAL USE
- Staff
- Personal communications are those made via a personal social media account. In all cases, where a personal account is used which associates itself with the school or impacts on the school, it must be made clear that the member of staff is not communicating on behalf of the school with an appropriate
- Personal communications which do not refer to or impact upon the school are outside the scope of this
- Where excessive personal use of social media in school is suspected, and considered to be interfering with relevant duties, disciplinary action may be taken
- The school permits reasonable and appropriate access to private social media
4.2. Pupils
- Staffs are not permitted to follow or engage with current or prior pupils of the school on any personal social media network
- The school’s education programme should enable the pupils to be safe and responsible users of social
- Pupils are encouraged to comment or post appropriately about the school. Any offensive or inappropriate comments will be resolved by the use of the school’s behaviour policy.
4.3. Parents/Carers
- If parents/carers have access to a school learning platform where posting or commenting is enabled, parents/carers will be informed about acceptable
- Parents/Carers are encouraged to comment or post appropriately about the school. In the event of any offensive or inappropriate comments being made, the school will ask the parent/carer to remove the post and invite them to discuss the issues in person. If necessary, refer parents to the school’s complaints
4.4. Monitoring posts about the school
- As part of active social media engagement, it is considered good practice to pro- actively monitor the Internet for public postings about the
- The school should effectively respond to social media comments made by others according to a defined policy or
Every effort has been made to ensure that the information contained within this policy is up to date and reflective of the latest legislative and statutory guidance. The online world is fast changing, and we recognise that areas of policy may need to be adapted and amended to reflect this. If errors are brought to our attention, we will correct them as soon as is practical.
This policy will be reviewed every two years or sooner, if necessary, to reflect legislative changes or developments, to ensure its continuing relevance and effectiveness.
POLICY APPROVED BY:
Headteacher SDL Chair
Mr G A Hussain Mr Sameer Abbas